As QR codes continue to power contactless payments, digital menus, marketing campaigns, and customer engagement, QR code security is now a key priority for companies of all sizes. Learning QR code security best practices and how to secure QR codes for business is critical to protect your brand and your customers from increasing digital risks. Cybercriminals are now using vulnerabilities found in QR codes to attack companies; organizations must act. You must take the above-mentioned proactive steps as a means of helping to prevent QR code phishing attacks and to ensure each scan remains a secure, trustworthy experience.
What Is QR Code Security?
QR code security refers to the protections and mechanisms in place to mitigate contactless attacks or malicious redirects from the QR codes themselves. QR codes function only in a one-way directional format, where the user scans the QR code without knowing a destination source before the interaction. So, it is crucial to have these security measures in place to eliminate or defer phishing attacks, fraud, and data loss. Implementing robust security measures for QR codes, businesses will know that each scan will take the user to a trusted or verified site.
Static vs Dynamic QR Codes: Which Option Offers Better Security?
Static QR codes have fixed informational properties and are not editable once created. That is easier for an attacker to duplicate or replace static QR codes. Dynamic QR codes allow operators to update content, monitor links in real-time, and enable analytics, which will offer security and more control for your promotional activity. Whether comparing them one-to-one or choosing from different types of QR codes, dynamic QR codes are always the safer of the two options if you’re considering payment, login, or promotional activity.
Key QR Code Security Risks That Lead to Phishing, Malware, and Fraud
Misuse of QR codes often takes advantage of vulnerabilities in QR codes, such as:
- Unsecure QR code generators, let alone insecure ones, can create revelatory codes.
- Physical tampering with real QR codes by placing them over other authentic QR codes.
- Redirects to malicious activity or phishing pages.
- Using hidden URLs or shortened URLs that obscure long and revelatory URLs.
With an understanding of risks, businesses can implement formidable departures of QR code security for customers and others while still protecting them from fraud.
Why Every Business Must Prioritize QR Code Security
Ensuring security around QR codes must be a concern for all businesses. In fact, cybercriminals are ramping up their use of malicious codes to compromise customer data, carry out financial fraud, and, frequently, distribute malware. Attackers often stick a fake QR sticker over a legitimate QR code, leaving it almost impossible for users to see that the QR code they are scanning is modified.
This increasing method of stealing information is called “QRishing,” whereby the victim links to a malicious site and unknowingly submits their log-in credentials, payment information, or other important data. It is important to note that this poses a risk not only to your customers but also to business devices, which can be compromised during a QR code-based attack; such attacks can threaten your business workflows and legal compliance as well.
Risks of Poor QR Code Security
The absence of QR Code protection puts your business at risk of multiple threats that can create long-term negative operational and financial consequences:
- Data theft and fraud: Criminal QR codes can take users to illegitimate and fraudulent websites where they capture credit card information, personal information, and login credentials.
- Malware and spyware infections: Criminals could use the QR code to directly download harmful apps, files, or tracking apps that compromise the user's device.
- Phishing attacks (Quishing): Victims could be directed to fake log-in pages for banking, email, or social media.
- Reputational damage: Customers subjected to fraud from unsafe QR codes may begin to disassociate from your brand.
- Internal IT risks: Your employees could scan a fake QR code that may have compromised your company's systems, caused downtime, or worse.
- Financial losses: Fraudulent transactions, legal fees, fines, or regulation sanctions and incident response will severely affect almost any business.
How Attackers Exploit QR Codes
Cybercriminals are relying on a few common themes when changing QR codes to trick unaware users:
- Physical tampering: Cheating QR stickers applied over a legitimate code in a public setting or high-traffic area (restaurants, parking meters, or retail displays).
- Shortened URLs: The use of manipulated URLs, disguised as shortened links, tricks users into visiting unsafe websites.
- Lack of destination validation: QR codes send users to the true URL, detected by the user, making them vulnerable.
How to Ensure QR Code Security for Your Business
A well-organized QR Code Security framework should be a joint undertaking between marketing, IT security, and legal. Marketing plans the experience and call to action, IT does the sanity check on what a QR code generator is and ongoing threat monitoring, while legal protects the QR code for compliance and data-protection rules, etc. A responsible QR Program Lead will formalize an arena for QR Codes, unifying QR security governance and managing the safe practice of QR Codes across campaigns.

Step 1-Clear Policies and Usage Restrictions
Start developing internal standards for when, where, and how you will deploy your QR codes. These policies prevent incidental misuse of the QR codes and promote consistent security practices across all customers and departments.
Your policy structure should include the following:
- Data Classification: Determine what data your QR codes may extract - customer data, payment activity, content about their preferences - and determine their sensitivity.
- Approved Placements: Establish where QR Codes can be placed (product labels, store signage, booths at events) and security restrictions such as dynamic QR Codes and expiration rules (time sensitive).
- Risk Thresholds: Ensure permitted use of QR codes aligns with your brand's reputational expectations in data privacy and compliance.
- Cross-Team Workflows: Plan a process where marketing, legal, compliance, and IT have specific roles in reviewing QR Code landing pages, potential redirects, and permissions prior to launching QR Codes.
- Governance documentation: Resources will be stored in a centralized manual addressing brand security to ensure all teams follow the same guidelines.
An established policy will provide businesses with appropriate QR code safety for their brand, drive compliance, and reduce the chance of tampering and misuse of data.
Step 2 - Choose A Secure QR Code Generator
Your platform choice will directly affect your success in preventing phishing, redirects, and unauthorized QR code use. A secure platform will also allow you to act quickly if you notice suspicious behavior.
Select a QR generator that:
- Utilizes HTTPS to protect all scan traffic.
- Has a privacy policy that is clear and aligns with GDPR and the world's data regulations.
- Provides dynamic QR codes, which allow links to be edited or disabled without the need to reprint.
- Gives you access to a real-time analysis of scanning and identifies potentially odd patterns.
- Export features give you content in formats like PNG, SVG, EPS, etc., for sharp printing and accurate scanning.
Regardless of whether a QR code generator is a paid service or a free QR code generator secured by its own controls, using a trusted platform can greatly reduce risks associated with phishing, malware, and fake redirects.
Step 3 - Design & Print With Security Top of Mind
Visual trust is a strong deterrent towards QR code fraud. Design QR codes using elements that will help your users, specifically your audience, to quickly identify your brand and the authenticity of a QR code.
Best practices include:
- Adding your brand logo, color border, or custom pattern.
- Add short vanity URLs next to the QR code for verification.
- Be sure to use a high-resolution format (PNG/SVG) to ensure scanning is clean.
- Use tamper-proof materials for sensitive deployments such as payment or login access points.
These design considerations help increase your credibility while making it easier for an attacker to present, overlay, or replace your legitimate QR codes.
Step 4: Implementing Placement & Life-Cycle Controls
Security extends well beyond the moment the QR code is created. You should protect your deployment environments the same way you are protecting digital assets.
Setup:
- Placement specifications: Approved indoor or outdoor environments, timeline for withdrawal (i.e., after an event), and once again, a well-lit installation area for the QR code to avoid tampering.
- Regular inspection schedules: Daily for high-risk deployment uses (payments/POS), weekly for static placements (posters/brochures).
- Versioning and tracking: Campaign IDs, UTM tags, or other means of unique dynamic URLs to help with management of updates and tracking performance, and to close expired campaigns.
By doing all of this, you reduce the chance of someone replacing or tampering with portions of your valid QR code, and you are much less likely to miss the fact that a change has taken place.
Step 5: Monitor Scan Activity & Identify Anomalies Quickly
Use the analytics feature of your generator to observe:
- Hourly and daily volume of scans
- Geographical activity
- Type of device used
- Conversion and bounce rates
- Irregular spikes, prolonged periods of inactivity, or redirection to a sudden 404 error
Automated anomaly alerts assist you in detecting possible QR code hacking threats sooner rather than later. If the platform has tracking capabilities (even a free QR code scanner with your analytics), you will be able to authenticate the QR codes when doing audits.
Step 6: Prepare a Quick Incident-Response Plan
When a QR code has been breached, time is of the essence.
Your plan should include:
- Immediate disabling of the QR code, or at least the ability to redirect the dynamic QR code to a safe web page.
- Redirect users to a secure information webpage rather than a generic error page.
- Fast notification procedures that notify IT, legal, and communications.
- Prepare transparent customer messaging that instills customer confidence without elevating concern.
Being proactive and having a rehearsal of an established response workflow will help protect your brand and trust while minimizing the impact of QR code misuse.
Effective Strategies to Prevent QR Code Hacking and Fraud
It is equally as important to develop ongoing security practices with policies in place. These ongoing measures help secure your active QR Code campaigns, follow through with tamper-proofing, and endorse ongoing user trust. When you layer operational discipline on innovative tools, your business may ultimately develop a more resilient QR Code Security program.
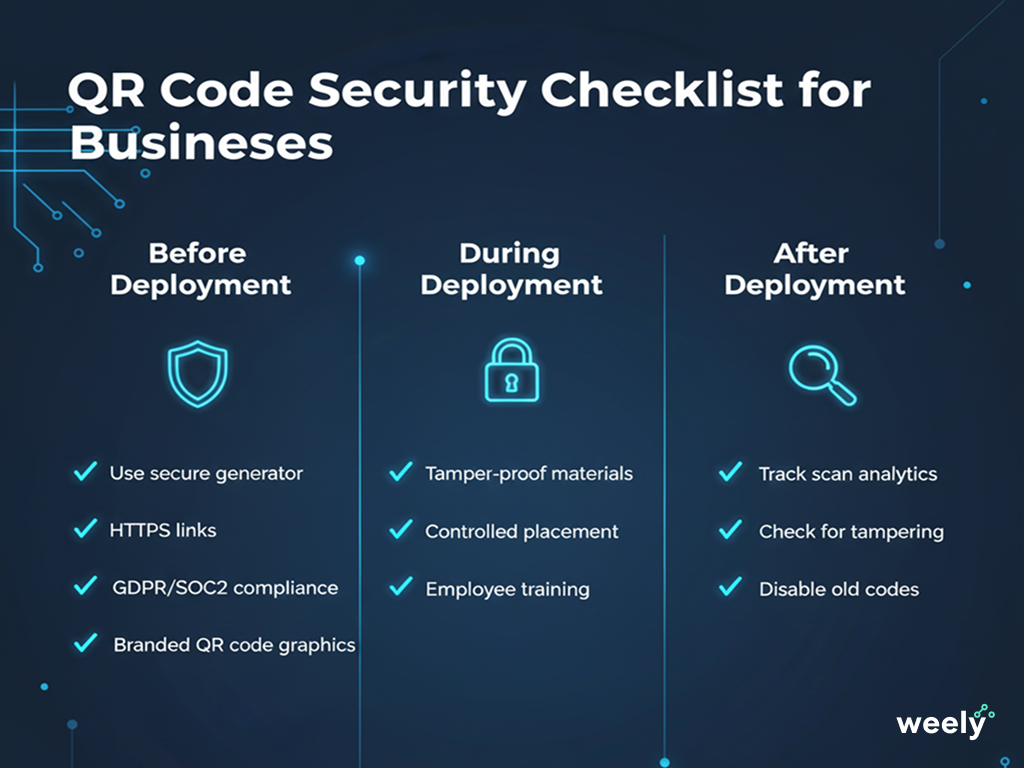
Verify Security Compliance and Platform Standards
Before activating any QR Code campaign, it is important to ensure that your QR Code generator is compliant with recognized industry standards. A secure QR code generator platform should provide:
- GDPR data processing compliance
- SOC 2 or ISO 27001 level security
- HIPAA or PCI compliant safeguards in place for sensitive data
- Encrypted scans and HTTPS
Using a company that has a trusted platform will help keep customer information safe, and using a QR Code Generator that offers a dynamic option, even a secure Free QR Code Generator tool, will help you feel more secure - at least you are putting systems in place to be proactive about keeping customer information secure.
Choose Dynamic QR Codes for Better Control
Dynamic QR codes allow real-time updates, redirects, and deactivation, which creates a unique advantage in QR code hacking prevention. Dynamic approaches are invaluable since they offer pulse check analytics to identify suspicious behavior. Realistically, dynamic formats offer a much greater strength of security for all types of QR codes, making them a great option over a static format.
Use Transparent CTAs to Strengthen Trust
Clear messaging helps customers feel safe when scanning. You can use CTAs like:
- “Scan to view menu”
- “Scan for product information”
- “Scan to complete a secure checkout process”
These CTAs prevent intruders from attempting to mimic your codes.
Train Staff to Identify Tampering
Frontline employees should be able to identify:
- Sticker overlays
- Unexpected colors or branding
- Complaints from a customer about being redirected unexpectedly
Employees can also check suspicious codes with a free QR code scanner.
Monitor Scan Patterns for Early Warning Signs
Set up alerts for odd scanning volumes, strange geographic patterns, or sudden upticks in engagement. Early detection allows you to shut down compromised QR codes before it escalates and impacts more users.
Strengthen Customer Confidence With Secure QR Code Experiences
The foundation of building trust with your audience starts with providing safe and predictable QR code experiences. When someone scans your QR codes, they are expecting authenticity, transparency, and protection from security risks. The QR code security practices you use can reinforce to users that each scan they initiate is both trustworthy and safe.
Consistency matters. A clear intent to the user, a branded or recognizable design, and secure redirect pathways will increase the likelihood the user will feel comfortable engaging with your QR codes across packaging, storefronts, marketing collateral, or service touchpoints.
Effective ways to strengthen trust:
- Every QR code should have a URL that is both encrypted and verified.
- Provide a short text to describe to users what the scan will do.
- Employ dynamic QR codes to change destinations in real time after scanning.
- Perform regular audits of systems and users to identify parsing activity or anomalies.
- Only place QR Codes in a controlled, secure, monitored environment.
Final Thoughts: Secure QR Codes Are the Foundation of Digital Trust
QR codes are a central connecting point when it comes to physical and digital experiences, making QR code security a necessary consideration for every modern business. When consumers encounter a QR code in a store, at a restaurant, during an event, or in the packaging of a product, they will provide the QR code with an implicit expectation of safety, clarity, and authenticity. As a result, using secure destinations for every QR code scan, performing regular checks, and providing strong visual cues helps to protect all consumers from tampering, phishing, or malicious redirects.
If businesses treat every QR code as seriously as they would treat any other digital property, they will mitigate their vulnerabilities and promote confidence among the users. A secure QR code system is one that considers protecting the customer's data but also recognizes that protecting the user is building trust in your brand. Protecting QR codes at the end of the day is about protecting trust, and trust is the basis for any long-term customer relationship.
Frequently Asked Questions About QR Code Security
Can QR codes be hacked, and how do businesses prevent QR code security breaches?
QR codes are not hacked, but the URL that you link to with a QR code can be modified and spoofed. Businesses can protect themselves against breaches by using a dynamic QR code with security protocol, links encrypted with HTTPS, and regular checks to identify stickers or tampering on QR codes.
What is the safest way to create QR codes for business use?
The most secure way to create QR codes is to use a secure QR code generator that also uses encryption, access controls, and analytics. This allows you or your organization to have oversight into scan behavior, deactivate any compromised QR codes instantly, and maintain a safe user experience.
How do I know whether a QR Code is safe before scanning it?
End users should check for indications of branding, an obvious call to action, and tamper-evident placement. Users should avoid codes that are displayed on random poles, ATMs, magnetic parking meters, or printed stickers with no context. They are the most susceptible to phishing attacks.
Are dynamic QR Codes safer than regular static QR Codes?
Yes. Dynamic QR codes with security tracking will allow you to change the URL of the underlying web code, disable the code if you notice unfamiliar, suspicious activity, and gather analytics on the scan process. Static QR codes cannot be changed after you print them and put businesses at a significantly higher security risk.
What are the most common QR code hacking methods businesses should know about?
While there are a variety of terms attackers use for QR code wrongdoing; they primarily rely on URL tampering of codes and sticker overlays, malicious redirection, shortened URLs and fake landing pages to optimize for QRishing (QR phishing attacks). Regular audits and solid governance policies help to minimize the risks associated with these tools.
What steps should my business follow to implement strong QR code security?
Start with usage policies, choosing a secure QR code provider, applying branded design, using dynamic QR codes, keeping analytics for monitoring, and training staff. These practices reduce organizations exposure to QR code fraud and malicious redirecting.




